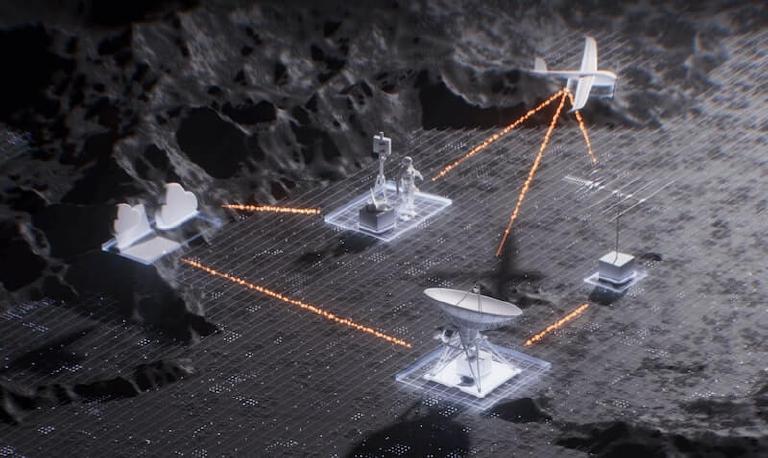
Themis
Cross-platform high-level cryptographic library
Themis helps to build simple and complex cryptographic features easily, quickly, and securely. It’s a perfect fit for multi-platform apps.
Themis hides cryptographic details and eliminates popular mistakes.
4 essential building blocks
Themis provides ready-made building blocks (“cryptosystems”) for secure data storage, message exchange, socket connections, and authentication.
Authenticated storage encryption
Secure Cell is a multi-mode cryptographic container suitable for storing anything from encrypted files to database records. Use Secure Cell to encrypt data at rest. Secure Cell is built around AES-256-GCM, AES-256-CTR.
Public key authenticated encryption
Secure Message is a simple encrypted messaging solution for the widest scope of applications. Use Secure Message to send encrypted and signed data from one user to another, from client to server, to prevent MITM attacks and avoid single secret leakage. Based on ECC + ECDSA / RSA + PSS + PKCS#7.
Zero knowledge proof authentication
Zero-knowledge proof-based protocol to compare secrets over non-trusted channels without risking leaks or reuse attacks. Use Secure Comparator for authenticating the users in a way that no password (or password hash) is sent over the network.
Session-based encryption
Secure Session is a session-oriented encrypted data exchange with forward secrecy for better security guarantees and more demanding infrastructures. Secure Session can perfectly function as socket encryption, session security, or a high-level messaging primitive (with some additional infrastructure like PKI). ECDH key agreement, ECC & AES encryption.
Join those who use Themis #
Industries and applications
- Mobile apps
- Fintech, banking, cryptowallets
- SaaS platforms
- Chats & messengers
- Cloud data encryption
- Documents exchange (VDR)
- Healthcare records exchange (EHR)
- Smart home & IoT
- Logistics & delivery services
- Any apps that operate on sensitive or personal data
Regulations
- GDPR
- DPB
- DPA encryption requirements
- CCPA
- FISMA
- HIPAA / HITECH Act
- PCI DSS
- PSD2
- FFIEC
- And others
Benefits
- Recommended by OWASP
- Solves 90% use cases for protecting data in mobile apps
- Implements application level encryption best practices
- 100% compatible across all supported languages
- Saves development time
- Hard to misuse, secure by default API
- Strong cryptography (trusted, verified, audited)
- No place for crypto mistakes. We tried hard to prevent ‘em.
One cryptographic library that fits ‘em all.
Themis is the best fit for multi-platform products (mobile, desktop and server-side apps) because it provides 100% compatible API and works in the same way across all supported platforms.
Perfect for client-side encryption, server-side encryption or building end-to-end encryption flows.
Typical usage scenarios #
Encrypt stored secrets
Store secrets (API keys, session tokens, files) encrypted in your apps and backends using authenticated symmetric encryption. Use Themis with iOS Keychain and Android KeyStore.
Share data between users
Exchange secrets securely: share sensitive data between parties, sign messages and verify signature, build simple chat applications with encryption in transit and at rest.
Zero knowledge proofs
Compare secrets between parties without revealing them by using interactive zero-knowledge proof-based protocol. Works best for authentication via insecure channels.
Field level encryption
Encrypt sensitive fields before storing in the database (“application level encryption”). Use searchable encryption, data tokenisation and masking with Themis and Acra.
End-to-end encryption layer
Build end-to-end encryption schemes with centralised or decentralised architecture: encrypt data locally on one app, use it encrypted everywhere, decrypt only for authenticated users.
Real-time encrypted sessions
Maintain real-time secure sessions: send encrypted messages to control connected devices via your app, receive real-time sensitive data streams from your apps to backends.
See Themis GitHub for more docs and examples.
Get started with Themis
Check Themis repository and docs for tutorials, how-tos and example apps.
Use Themis to implement application level encryption best practices.
Unified API for all platforms: easy to use, hard to misuse. #
Themis provides 100% interoperability across supported platforms, respects backwards compatibility and stability: your app won’t be broken because some npm package is missing.
Contact us
Interested in consultancy or commercial support? Let's talk.
We can help you with building custom cryptographic solution using Themis, designing and building end-to-end encryption or partially encryption schemes, or chatting with your engineers about the best AES mode :)