Conferences & events
Members of the Cossack Labs team often participate in international security and development conferences as speakers, organise and co-organise local events, conduct public workshops and private trainings, and support communities (CocoaHeads, Women Who Code, OWASP).
You can read more in our blog, LinkedIn, Facebook, Twitter, and DEV. Below you can find a collection of video recaps and speaker slides from such events.
Building Security Protections for Robotic Devices
Anastasiia Voitova described the multi-layered security of a modern robotic and autonomous system designed to protect devices and their data. Building defence-in-depth measures include operating system hardening, automated secure device provisioning pipelines, unambiguous device identification, data security for telemetry and commands, secure over-the-air updates, active reverse engineering protections, reducing human involvement, and more.
Secure architecture for mission-critical systems
Anastasiia Voitova, Head of Security Engineering at Cossack Labs, talked at the DOU Day offline conference about building secure architecture for mission-critical applications. Anastasiia focused on reinforcing the resilience of critical systems to make them secure and reliable.

Bulletproof your software: The magic of security autotests
Product security is a process, and some of the steps could be automated to save resources and prevent security regressions. Our Security Engineer, Elmir Iskanderov, talked about his experience and ways to speed up product updates through automation at the Online QADay conference.
Building data-centric security controls for mission-critical applications
Head of Security Engineering Anastasiia Voitova shared unique expertise on building resilient security controls for mission-critical applications and defending nation-wide infrastructures from cybersecurity threats at NATO TIDE Sprint 2024 event, held by NATO Allied Command Transformation.

Critical Infrastructure Cybersecurity Diagnostics: Strengthening Digital Protection
Cossack Labs participates in the discussion of current issues of assessing the state of cybersecurity of critical infrastructure and took part in the “Critical Infrastructure Cybersecurity Diagnostics: Strengthening Digital Protection” conference. The conference was held by USAID Cybersecurity Activity, the State Service for Special Communications and Information Protection of Ukraine and the Ministry of Digital Transformation of Ukraine.
The talks focused on critical infrastructure cyber defence enhancement as part of the USAID-supported Program for diagnosing cybersecurity status of critical infrastructure operators. The Program is based on the updated NIST Cybersecurity Framework 2.0 from National Standards and Technology Institute.
 Ihor Malchenyuk at “Critical Infrastructure Cybersecurity Diagnostics: Strengthening Digital Protection” conference
Ihor Malchenyuk at “Critical Infrastructure Cybersecurity Diagnostics: Strengthening Digital Protection” conferenceInvestments in Cybersecurity in the CEE region
Ihor Malchenyuk, Head of Customer Solutions at Cossack Labs, spoke at the CYBERSEC FORUM/EXPO 2023 panel “Investments in Cybersecurity in the CEE Region.”
Ihor discussed cybersecurity challenges in the CEE region, such as the growing number of malware and ransomware attacks, the increased focus on users/people and endpoints, the rising cost of data breaches, the expansion of privacy regulations, and cyberwarfare against mission-critical applications and critical infrastructure assets.
The main conclusion—a lot of pressure from a very dynamic threat landscape, lessons learned from current cyber warfare, and legislation to encourage businesses to practise healthy cyber hygiene create a market opportunity for cooperation between governments and businesses to address the challenges.
 Panel discussion “Investments in Cybersecurity in the CEE region.”
Panel discussion “Investments in Cybersecurity in the CEE region.”Crypto wallets security for developers
Why cryptocurrency wallets security is not about blockchain but about application security and user education? What crypto wallets and banking apps have in common? Are they as secure as banking apps? In her new talk, Julia goes into details, risks and threats of crypto wallets, design concerns and implementation issues, and gives practical advice for developers who want to make their apps more secure.
The secret life of Android apps
In his talk for the OWASP Zhytomyr community, Artur uncovers solutions to practical security issues every security engineer faces. The mobile application landscape is constantly changing – developers use new frameworks, Google demands new requirements and security features. Artur demonstrates the latest setup of a lab environment for security testing of Android apps. He uses it to illustrate how different apps implement specific OWASP MASVS requirements — like certificate pinning or root protection. Artur shows where to look to spot the missing security controls.
Data is a new security boundary
As a keynote speaker of this flagship event by OWASP, Anastasiia explains how developers and companies use cutting-edge cryptography and data security approaches when no perimeters and trusted zones exist anymore. In this talk, she starts with data security 101 and gets you through peculiarities of application level encryption (ALE), end-to-end encryption (E2EE), searchable encryption, zero knowledge architectures and zero trust. She demonstrates real-world cases of integrating application level encryption and supporting traditional security controls to protect customers’ data. By the end of the talk, you can have a whole picture how “strong cryptography” becomes “real-world security boundary around sensitive data” and what it takes in different contexts.
React Native security: addressing typical mistakes
Can React Native apps be secure? Is it a leaky abstraction? Julia went in details of React Native architecture, platform usage, and its dependencies. This security talk is designed specially for developers, decision-makers, and tech leads interested in addressing and preventing typical mistakes related to this cross-platform solution from Facebook.
 Sketch of Julia's NSSpain talk by felibe444
Sketch of Julia's NSSpain talk by felibe444Cryptographic protection of ML models
The security challenge is to protect ML models from leakage and massive accumulation, which leads to reverse engineering of unique IP. In this talk, Anastasiia explains building DRM-like protection with application level encryption using HPKE-like approach on ephemeral keys. She discusses risks, threats, dataflow, cryptographic layer, key management and integration with traditional application security controls for defense-in-depth approach.
 Slide from Anastasiia's talk about ML models protection by means of cryptography
Slide from Anastasiia's talk about ML models protection by means of cryptographyThe art of secure architecture
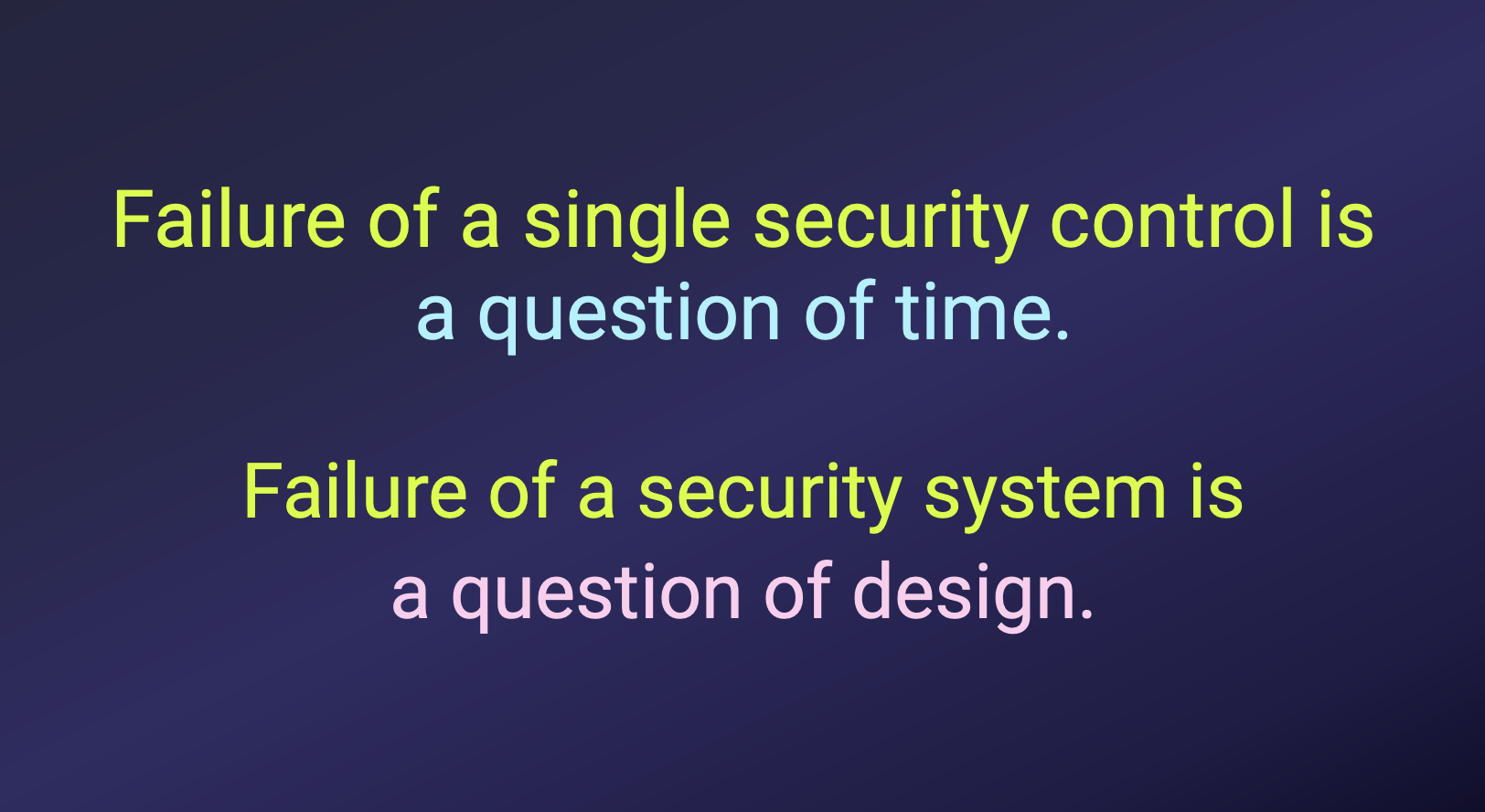
Secure architecture is about decision making. Learn from Julia how it differs from secure coding and what you can do for your developer team to achieve better results while following SSDLC.
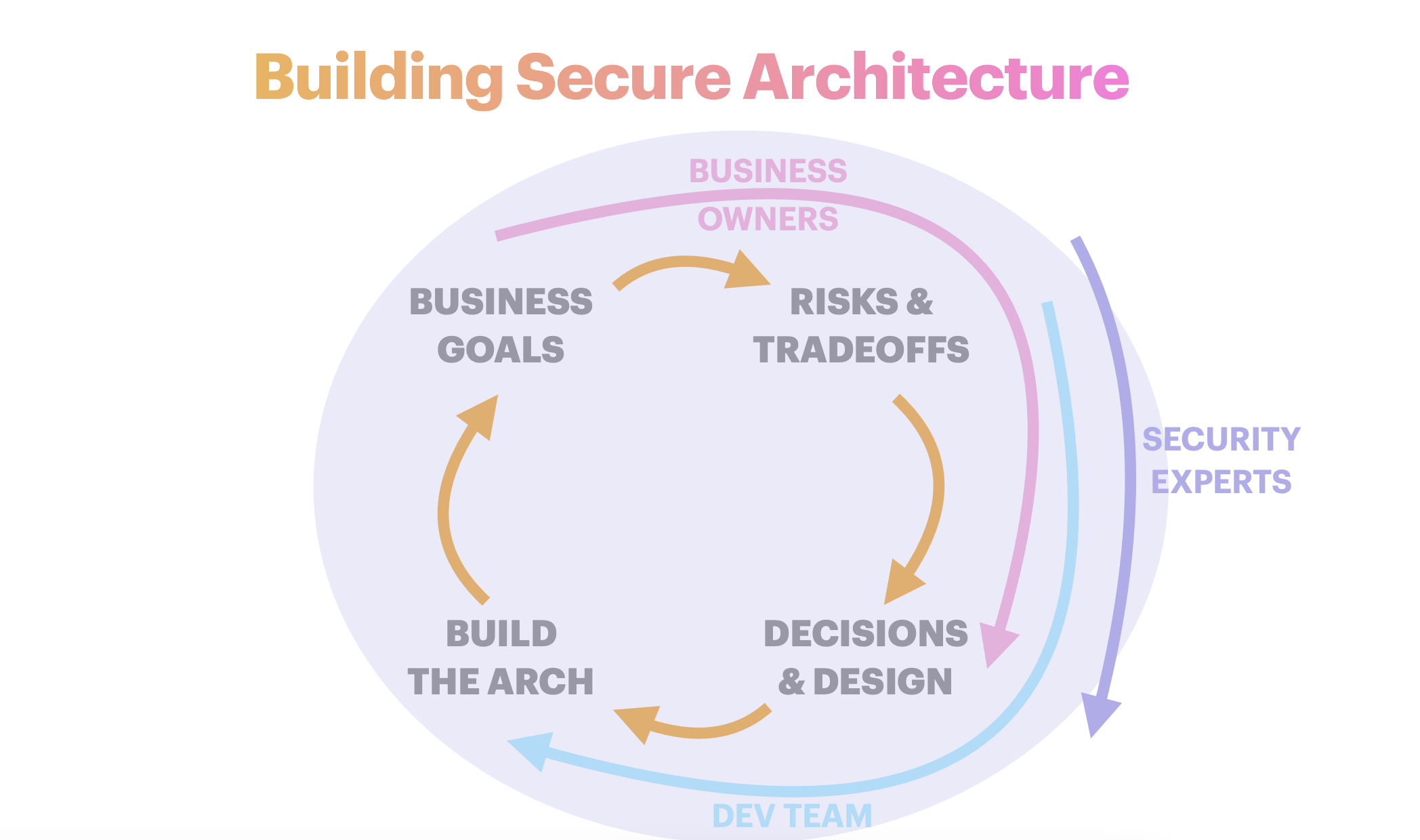 Slide from Julia's talk about security architecture and tradeoffs
Slide from Julia's talk about security architecture and tradeoffsEncryption export regulations. Why should mobile developers care?
Julia talks about US encryption export regulations - what they mean, which applications they affect, and what developers should do.
iOS vulnerabilities and how to fix them
In this talk, Julia invites app devs and architects to explore common iOS vulnerabilities, outlines popular requirements from OWASP MASVS, enlists examples and paths to make applications more secure.
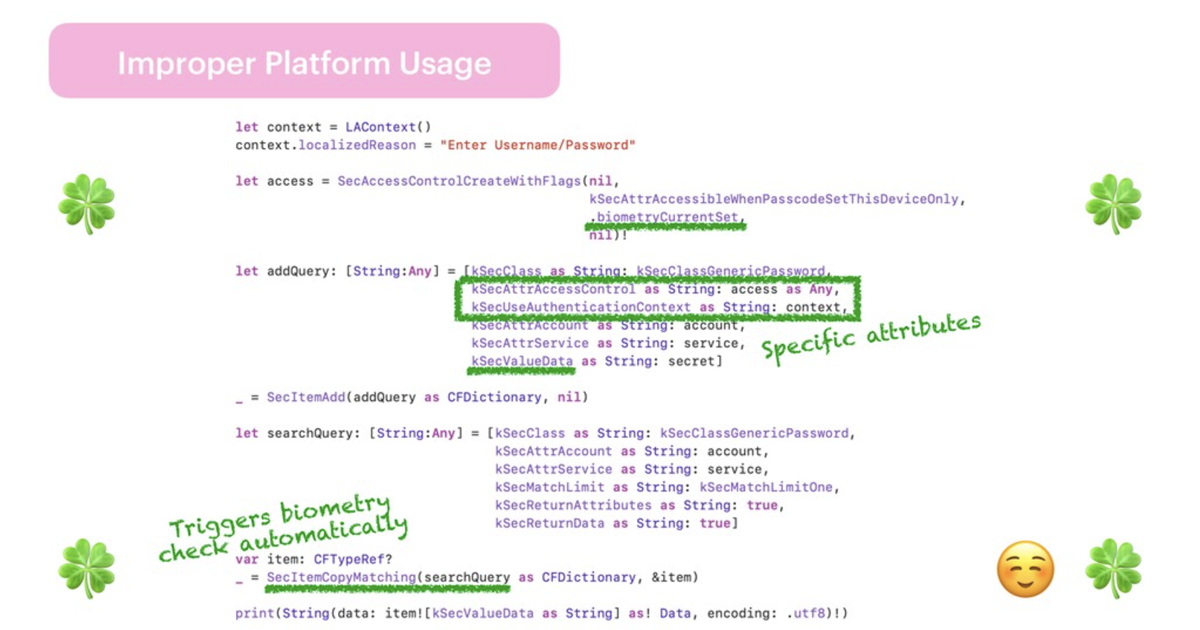 Slide from Julia's talk about improper usage of biometric authentication API
Slide from Julia's talk about improper usage of biometric authentication APIEnd-to-end encrypted doesn't mean secure
End-to-end encryption doesn’t guarantee privacy and/or security of your data. Your favourite application can use e2ee and sell data to someone at the same time. Anastasiia explained the relationship between security, privacy and encryption, and how different encryption approaches protect users data from various events or threats.
Secure Authentication. Are you sure you do it right?
Julia unraveled security issues developers should keep in mind to implement SSDLC, gave clues to the secure authentication standards, and shared experience on how to avoid typical auth mistakes in iOS apps.
Use cryptography, don’t learn it
Anastasiia gave a small hardcore cryptographic session and covered usable cryptography and the scenarios which can help app developers to right up their ship in case of cryptography or data security tools misuse. Get in details why boring crypto is actually better than “fun” crypto.
 Eugene @ QCon London 2020
Eugene @ QCon London 2020Designing secure architectures the modern way, regardless of stack
Eugene talked about implementing sophisticated defences in constrained environments: ranging from protecting massive power grid SCADA networks to improving end-to-end encryption in small mobile applications. Technological stack doesn’t matter if you focus on the risk assets and design defences around asset lifecycle.
Protecting data in ICS, SCADA and industrial IoT: goals, problems, solutions
Eugene shared our experience and lessons learnt of building secure data aggregation systems with hardware-based encryption, time-series processing and end-to-end security. Learn about our solutions that are integrated into ICS/SCADA networks of industrial operators, extract sensitive data, encrypt it “on the fly” and process separately.
 Eugene @ UA.SC
Eugene @ UA.SCSecurity engineering: from encryption to software architecture patterns
Public training on security and cryptography engineering conducted jointly by Anastasiia and Jean-Philippe. We focused on solving practical security engineering challenges rather than academic cryptography. We talked about SSDLC and risk management, cryptography and typical cryptographic mistakes, using and misusing APIs, building defence-in-depth for distributed applications.
Maintaining cryptographic library for 12 languages
Maintaining cross-platform cryptographic library is a journey full of unexpected bugs, language-specific hacks, difficult decisions and the endless struggle to make developer-facing APIs easy-to-use and hard-to-misuse. Anastasiia described the four years journey of designing and supporting Themis: from shaping cryptosystems, writing language wrappers to CICD pipelines, autotests and interactive documentation.
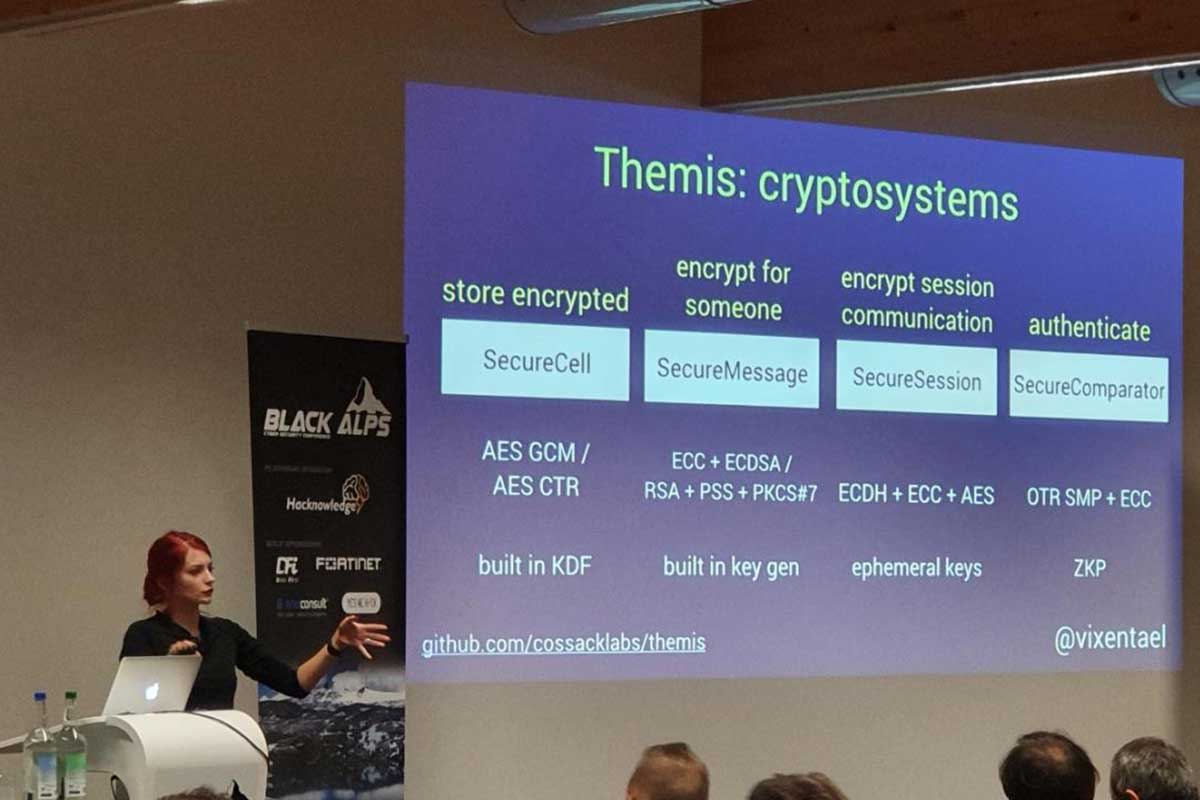 Anastasiia @ BlackAlps
Anastasiia @ BlackAlpsDesigning secure architectures, the modern way
In this talk, Eugene tried to cross the bridge between modern DevOps/SRE practices, systems architecture design and traditional security/risk management. It is driven by lessons learnt from building systems the modern way in high-risk environments with high reliability and security demands, drawing from the experience of protecting governmental secrets, critical infrastructure and preventing banking fraud at scale..
 Eugene and Anastasiia taking part in panel discussion @ Devops Stage
Eugene and Anastasiia taking part in panel discussion @ Devops StageBuilding SQL firewall: insights from developers
How SQL firewalls can help to protect databases from SQL injections: the main difference from web application firewalls (WAFs), common usage scenarios, pros, and cons. We implemented SQL firewall as part of data encryption proxy Acra, and we will share insights about security and development decisions. Expect a story about parsing SQL protocols, matching rules, hidden dangers of logging, best of configuration and usage patterns.
 Artem @ Fwdays Highload
Artem @ Fwdays Highload10 ways open source will hurt security and reliability
We all know how open source is useful. In this talk, Eugene describes the obvious and not very obvious risks that open source brings with it and what are the practical consequences. Learn what you need to pay attention to when selecting components for your new spacecraft to protect it from exploding during takeoff.
10 lines of encryption, 1500 lines of key management
Watch a story behind implementing end-to-end encryption for Bear application. Anastasiia explained the security engineering flow: protocol design, selecting cryptographic library, cryptocoding techniques, building defence-in-depth and preparing for incidents. Learn how to build an encryption engine for the app with 6M users.
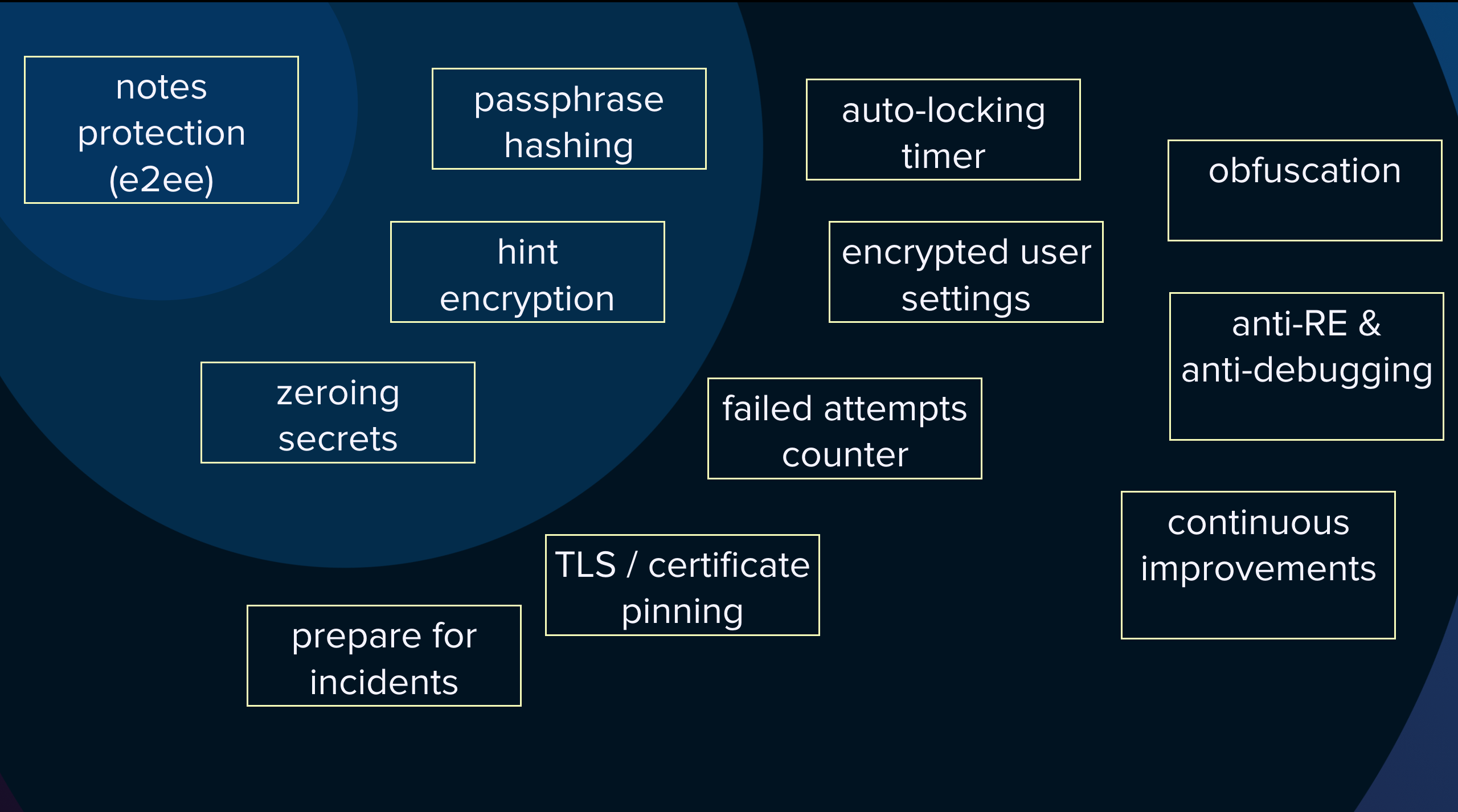 Slide from Anastasiia's talk with lines of defense around end-to-end encrypted notes
Slide from Anastasiia's talk with lines of defense around end-to-end encrypted notesDisagree with "I Agree". Enforcing Better GDPR Compliance Through API Documentation
The talk addresses the aspects and elements of API documentation that need to be reconsidered and restyled in the light of GDPR. The way things are, an absolute GDPR compliance is impossible, but maximal compliance is doable. Technical writers can enforce it through the language graphic elements that are used for guiding the users around the API portals.
Security, privacy and cryptography at WWDC19
Apple made many announcements on WWDC 2019 about cryptography, cybersecurity and privacy. Anastasiia highlighted important changes for developers – including new CryptoKit framework, data privacy regulations, new app permissions.
Search over encrypted records: from academic dreams to production-ready tool
The search over encrypted data is the modern cryptographic engineering problem. We will talk about existing approaches (both well-known and modern), and concentrate on practical solution based on blind index technique to search data in databases. What’s inside: cryptographic and functional schemes, implementation details, practical security evaluation (risk modelling and potential attacks). We will show how theoretical models turn into real, usable, maintainable, security tools. Search over encrypted records is part of Acra encryption proxy.
 Artem Storozhuk @ NoNameCon
Artem Storozhuk @ NoNameCon"Defense in depth": trench warfare principles for building secure distributed applications
“Defense in depth” is a security engineering pattern, that suggests building an independent set of security controls aimed at mitigating more risks even if the attacker crosses the outer perimeter. During the talk, Anastasiia modeled threats and risks for the modern distributed application, and improved it by building multiple lines of defence. She gave an overview of high-level patterns and exact tools how to build defense in depth for your distributed web applications.
Code injections using ptrace
Have you ever used dynamic libraries before? We’re sure you did. Alexei explains how OS loads dynamic libraries and how to load another library instead (using LD_PRELOAD hooks). As it’s easy to detect and mitigate LD_PRELOAD, Alexei digs deeper and talks about code injection on runtime. Learn how to use ptrace to search functions in a memory-mapped process and to manipulate the process’s state and thread execution.
Secure software development: from rookie to hardcore in 90 minutes [workshop]
A workshop for iOS developers that illustrates typical mistakes they do trying to implement security into their apps. Anastasiia showed an actionable to-do list of things developers might want to improve in their apps, and gave a set of key management techniques for mobile apps.
 Anastasiia Voitova
Anastasiia VoitovaDelivering security products without shooting yourself in the foot
Dmytro Shapovalov, our senior infrastructure engineer, talks about improving the infrastructure for developing, testing, and delivering security tools. Our experience of smoothing the difference between security idealism and engineering friendliness.
 Dmytro Shapovalov @ SecurityBSides Kyiv
Dmytro Shapovalov @ SecurityBSides KyivTeach your application eloquence. Logs, metrics, traces.
Most modern applications live in a close cooperation with each other. Dmytro spoke about the ways to effectively use the modern techniques for monitoring the health of applications. Being an infrastructure engineer, Dmytro explain typical mistakes developers do when implement monitoring, and suggested a couple of approaches and tools that can help.
 Dmytro Shapovalov @ RubyMeditation
Dmytro Shapovalov @ RubyMeditationData encryption for Ruby web applications
Making secure applications is not easy, especially when encryption tools are difficult and incomprehensible. Dmytro talked about typical data security problems in web apps and about proper implementation of encryption. Dmytro reviewed the cryptographic approaches and the exact tools that ensure that no sensitive data leaks from the application or the database.
Cryptography & data security: protecting the data while reducing cost in distributed systems
Using cryptography for data protection is not exclusively reserved for “secure chats” and financial products. Modern cryptographic tools help to comply with the regulations and laws, help to improve control over the infrastructure, to prevent data leakages, and to reduce the risk of incidents. Eugene talked about the way modern cryptographic tools allow technology companies to reduce the security budget and to remain protected at the same time.
 Anastasiia Voitova @ JavaZone
Anastasiia Voitova @ JavaZoneDefensive team – who are the security engineers and how they help teams to develop secure applications
Who are the people in the “blue team” and how do they prevent business risks for company assets? What is secure development, secure architecture, secure coding? A lecture for Women in Appsec Kyiv community and infosec students.
 Cossack Labs people @ NoNameCon
Cossack Labs people @ NoNameConMarrying usability and security in large-scale infrastructures
Usability is often thought of as the opposite of security. However, most of the security controls inside operating systems and most of the security tools that run there are designed for being operated by humans. This talk is a summary of Eugene’s experience in building and seeing engineers integrate the security tooling – how security controls and tools are mis-designed and fail once used, how poorly integrated controls decrease the overall security of a system, and how lessons learned in reliability/infrastructure engineering apply to security tooling to fix that.
Protecting sensitive data in modern multi-component systems
A talk for solution architects and technical leads, in which we took a deep look into data lifecycle, risk, trust, and how they affect security architecture, encryption, and key management techniques. We illustrated typical SDL patterns: narrowing trust, monitoring intrusions, zero knowledge architectures, distributing trust. The goal of the talk was to provide a general thinking framework and enough ideas about tools for senior engineers for them to be able to plan their solutions securely, in relation to the sensitive data inside.
 Karen Sawrey @ API The Docs Amsterdam
Karen Sawrey @ API The Docs AmsterdamZero Knowledge Architecture Approach for Mobile Developers [workshop]
A workshop for iOS developers that illustrates how to implement end-to-end encryption of Firebase notes application. Zero knowledge algorithms and protocols ensure that no keys, passwords, files, or any other sensitive material ever gets transferred in an unencrypted or reversible form. Workshop code contains two encryption schemes and set of general recommendations of improving security of any iOS application.
Making security usable: product engineer perspective
This is a story of going over the typical security challenges: how to build products that reliably deliver security guarantees, how to avoid the typical pitfalls, and how to create tools that could be usable and predictable for real users. It’s a tale of balancing religious adherence to security practices while keeping the customers’ needs in mind all the time, inside the development team; a story of listening to the customers and observing the actual user behaviour outside in the wild, and trying to make the best decisions when it comes to empowering the customers with easy tools for encrypting data in their apps, securely and without pain. Presented for senior software engineers at QConNYC.
Getting secure against challenges or getting security challenges done
What it takes to make security decisions in a business environment, from the perspectives of both vendor and client, urging security engineers not only to think outside the technical box but also outside the box of engineering thinking when faced with real humans on the other side of the wire. Presented for security engineers at NoNameCon.
 Eugene Pilyankevich
Eugene PilyankevichDocumenting the secret
A talk for Women Techmakers Lviv on creating and maintaining documentation for cryptographic software. Besides the issues of information security, such things as basic self-care and sanity were also brought up. This talk was also given in December 2017 at the one-day API The Docs Amsterdam conference.
X things you need to know before implementing cryptography
A “tips and tricks” talk for mobile developers. Even when developers create apps with security in mind, (at least try to) protect user secrets, and don’t reveal unencrypted data, attackers can still find ways to bypass these security measures by exploiting architectural weaknesses and non-obvious, yet very simple vulnerabilities. The talk is about all the tiny bits and pieces that are necessary for making your app secure against simple attacks way before focusing on the hard things (like cryptography).
Encryption without magic, risk management without pain
An in-depth technical inquiry about cryptography in a wider context: how it helps to narrow more significant risks to controllable attack surfaces, enables efficient and elegant risk management, and how tools and algorithms sit in a broader context of managing infrastructure-wide risks associated with handling the sensitive data.
 Karen Sawrey
Karen SawreyThe Bad, The Ugly, The Good
Karen Sawrey, our technical writer, gave a talk on refactoring the existing GitHub documentation of our products and moving it to our own proprietary documentation server.
GDPR – Get security done
We co-organised a security meetup for Ukrainian companies to discuss the various technical aspects of GDPR. Our speakers gave two talks, outlining various aspects of GDPR demands and possible compliance tactics.
 Eugene Pilyankevich @ OSDN Kyiv explaining Data encryption
Eugene Pilyankevich @ OSDN Kyiv explaining Data encryptionZero-knowledge architectures for mobile applications
The talk focused on real-world problems that ZKA counters, typical cryptographic designs and progress in different spheres of ZKA. The talk also explained the practical approaches useful for mobile developers (implementing data sharing and user collaboration on data in a cloud in a way that makes a mobile app provably secure).
 Anastasiia Voitova @ NoNameCon
Anastasiia Voitova @ NoNameConKey management approaches for mobile applications
Trust is built around various trust tokens: keys, passwords, secrets, biometric properties, things you have and things you know. Key management is complicated when done the right way.
DevOps and security: from the trenches to command centers
DevOps movement emerged as an attempt to build the bridge between people who write code, people who maintain the infrastructure for running it, and people who make the business decisions. These changes have put the emphasis on the new set of techniques and values. These techniques and values can either be beneficial or problematic for the security posture.
End-to-end data turnover: building Zero-knowledge software
Our CTO’s talk on the evolution of end-to-end software, survival within the “everything will be broken” model with the help of employing proper cryptography and trust management, plus a disclosure of some ideas and concepts behind Hermes.
 Eugene Pilyankevich
Eugene PilyankevichEverything will be broken
Our CTO’s talk about the classic and emerging threat models, a proper understanding of security risks, perception of technical infrastructures ranging from idealistic to realistic, and adopting stronger techniques in the face of the vanishing perimeter and the (sadly) lowering standards of security tools and overall quality of the produced software.
Evolution of password-based authentication systems
These are the slides that accompanied the talk of our core scientific contributor. The talk is focused on on evolving from regular authentication to Zero-Knowledge Proofs (including with Secure Comparator) at DefCon Crypto Village.