
Cloud data security solutions
Data security in a cloud is based on a risk sharing approach: cloud providers cover some security concerns, but the application owner is still responsible for the data security inside the application and some of the infrastructure security settings.
Having less things to worry about, but also less control impacts security posture and creates unique requirements for orchestrating data security controls. Things get especially tricky in a multi-cloud environment. Learn below about data security challenges in cloud computing and their solutions.
Cloud data security challenges
BYOK / HYOK challenges
Enterprise customers expect that their sensitive data is encrypted by unique keys. It’s achieved with Bring Your Own Key or Hold Your Own Key schemes. The challenge of BYOK / HYOK is to build key management procedures depending on who is responsible for key storage and backup—the customers themselves or the solution provider.
Gap in available cloud security controls
It is still necessary to maintain application security and eliminate data breaches as the data owner is responsible for data privacy in the cloud. Useful cloud security controls include field level encryption (protects sensitive data from developers and DBAs); firewalling and SQL injection protection; audit logging to restore the picture in case of an incident.
Managing complexity
The biggest cloud data security challenge is managing complexity. Moving data through several services, using multi-cloud or hybrid cloud requires more refined access policies and configurations to coordinate different data security controls.
Vendor lock-in and cloud migration
When moving between clouds, migrating cloud-specific controls, configurations and keys becomes a challenge. Even cloud-agnostic tools require re-deployment. Migration means massive risk exposure of spillover and risk of misconfigurations along the way.
Modern cloud data security solutions
Cover cloud security risks with fewer tools
Mitigating security risks with fewer tools decreases a number of bugs and narrows down the attack surface. It’s also easier to orchestrate security policy over dozens, not hundreds, components.
Scalability and security
The cloud data security layer should not prevent scaling and efficient maintenance of your cloud solution. The data security layer could take many shapes: a transparent database encryption proxy, encryption-as-a-service API, or client-side SDK.
Developer friendly tools
Cloud data security tools should be easy to integrate, easy to deploy, easy to configure and use. They should work with popular programming frameworks, databases and BI tools.
Our offerings
// Cloud data security software
Acra
A DATABASE SECURITY SUITE
To be announced
// Custom solutions and consulting
Tamper-free audit logs
Security engineering
Security advisory
Have a question? Get a human to answer it!
Benefits of our cloud security solutions
Cloud platform compatibility
Our cloud data security solution supports all cloud computing platforms (DigitalOcean, AWS, GCP, Heroku, Azure). Acra is cloud-agnostic, which makes protecting data in multi-cloud or hybrid environments as easy as deploying one container.
Fast time to solution
Acra is easy to integrate, easy to configure and run without significant interruption of the existing architecture. Acra is perfect for solutions that process sensitive data and value time-to-market.
Reduce risks and burden with engineering assistance
Our customer success program fits each use case – whether it’s configuring our products, building a custom solution, or analysing security architecture – we are here to lift this burden off you. We provide security engineering consulting, ongoing support and monitoring under fixed SLAs to ensure that you retain maximum security benefits from using our products and services.
Cloud data security in use
Data security in a cloud requires specific thinking, as data is everywhere: apps, databases, logs, 3rd party services, etc. Data security tools like Acra help to build a cloud-agnostic security layer, protecting data whenever it exists. Cloud security becomes an orchestration of tools, policies and processes spread across all places where data appears.
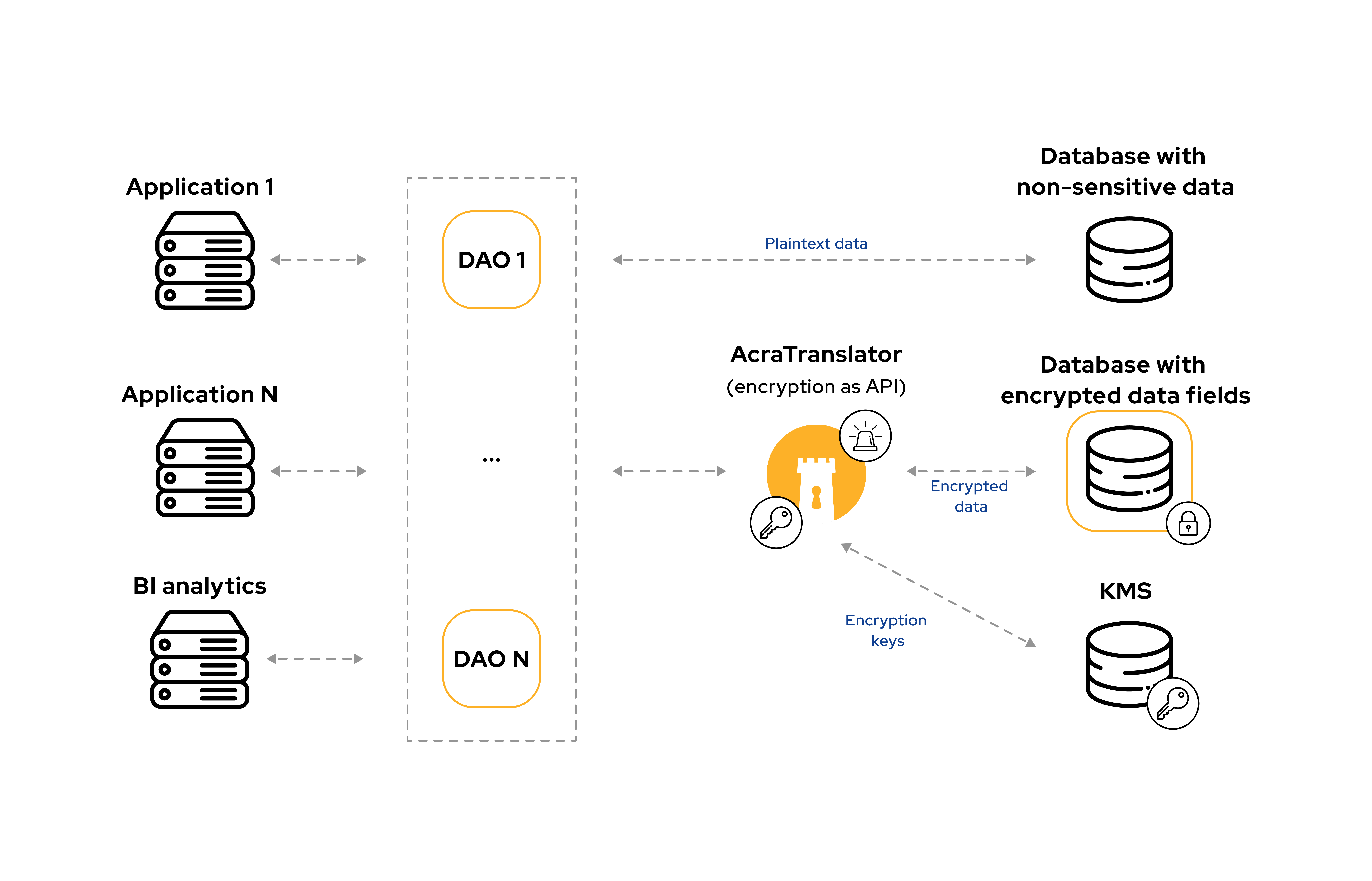
Take a look at this Data Access Object (DAO) architecture as example. A DAO is a service that proxies data exchange between backend services and multiple databases. The DAO controls the dataflow: it knows which data is sensitive and where it's stored, which data fields should be encrypted/decrypted during each request.
Often, the DAO also authenticates applications, and provides high availability.
On the scheme below the DAO calls Acra as encryption service to encrypt/decrypt sensitive data fields. Acra is responsible for key management and audit logging.
Additional relevant materials
The keynote 'Data is a new security boundary' is presented by Anastasiia Voitova at OWASP Global AppSec US 2021. Anastasiia explains how modern data protection combines multiple security controls and follows sensitive data where it exists – from client-side apps to the databases. The YouTube video is available as well.
For innovators, by innovators
We've started Cossack Labs to develop new tools and methods for protecting the data and enabling novel solutions to emerging problems — so that at the edge of your innovation, you’ve already got fitting tools handy.
Contact us
There are many ways we can help: with our products, bespoke solutions, and engineering services. Leave your contact information to connect with our team:
Relevant blogposts

Shared responsibility model in cloud security: mind the gap
Security responsibility of cloud providers: where it ends, what are the gaps, and what steps your team should make to improve cloud security strategy.

TLS certificate validation in Golang: CRL & OCSP examples
All developers need to know about using OCSP and CRL for validating TLS certificates in Go apps. Things we’ve learnt while building our own OCSP/CRL validation tooling: design, implementation and security tips, example code and popular mistakes.
