Hermes
Zero trust, end-to-end encrypted, secure data storage and sharing framework
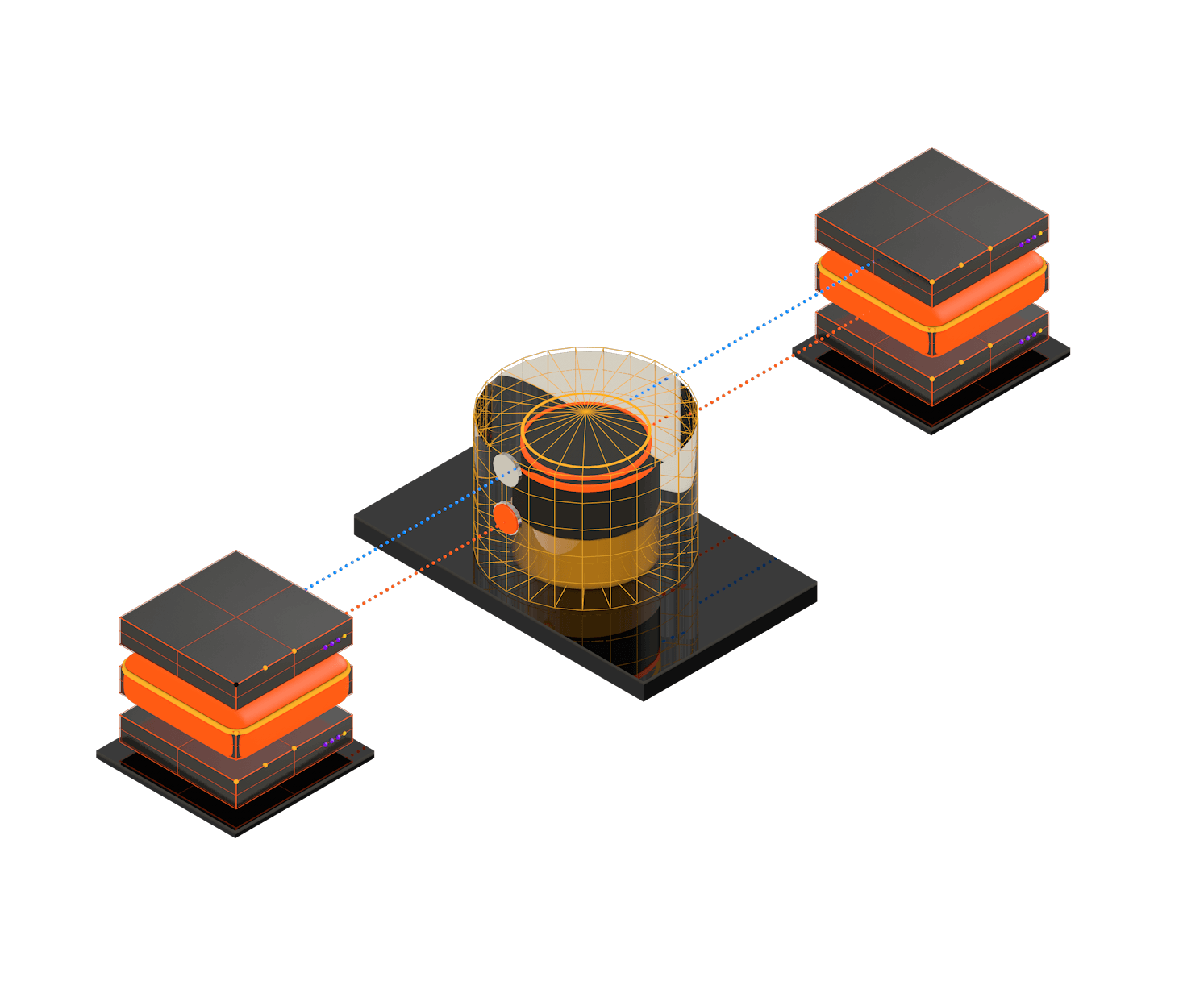
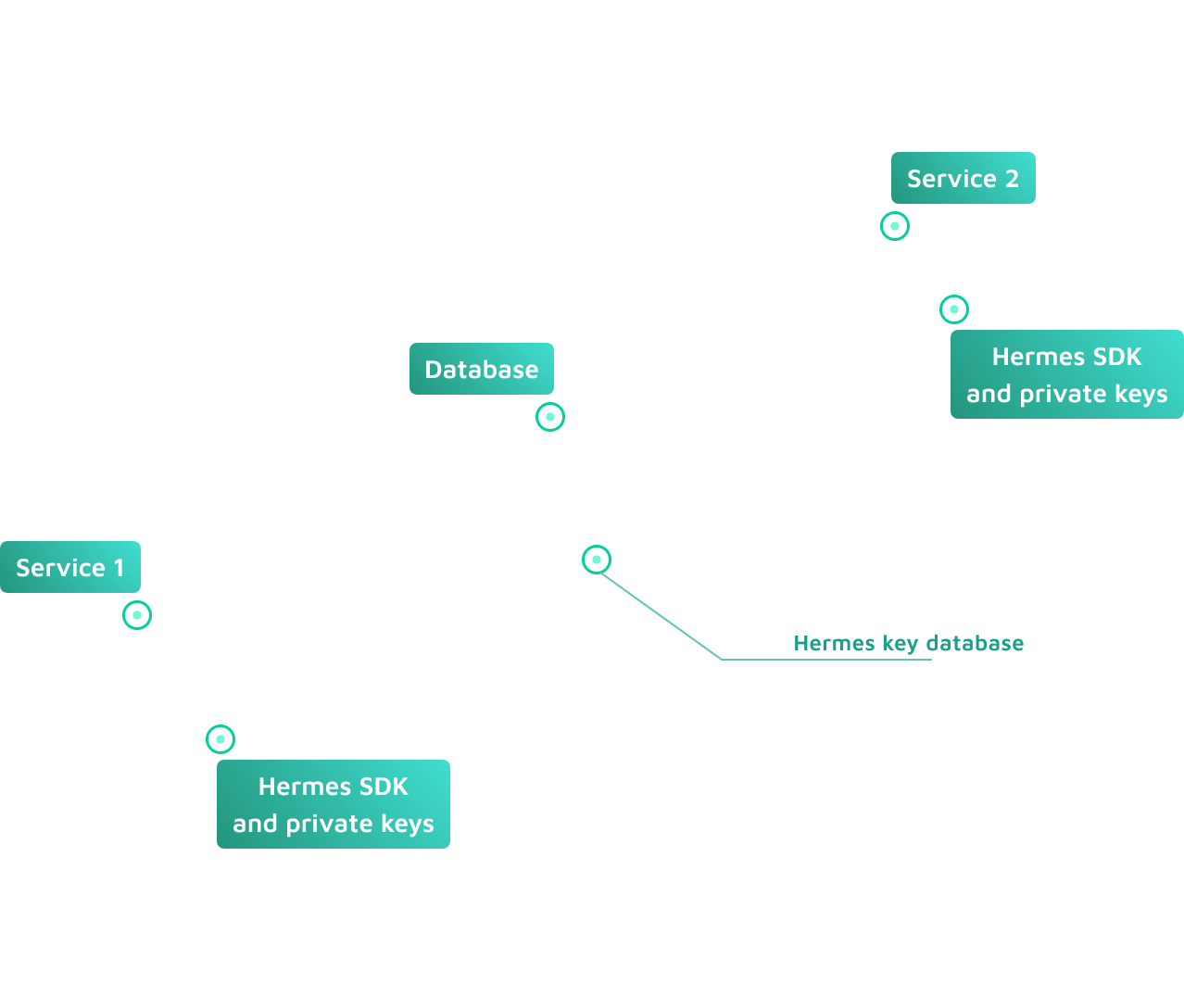
Enforce access control and facilitate sharing with end-to-end encryption via client-side SDK. Hermes provides cryptographically protected data processing and data collaborating without the need to re-encrypt an excessive amount of data.
A simple way of collaborating on end-to-end encrypted data
Industries
Hermes’ unique capabilities are the best to protect shared structured documents, where different fields have different security risks and access control patterns.
Finance
Healthcare
Enterprise
Advanced use-cases
Get started with Hermes
See Hermes documentation for more info and how-tos
Related materials

How mobile app analytics library led to the PII exposure
Vulnerabilities in third-party libraries: Exploring a real-world case where an update in an analytics library exposed personal data. We’ll cover the entire journey from discovering the i...

SBOM from the security perspective
Despite being a potential approach for enhancing software supply chain security, SBOM’s own flaws and complexities in implementation may be holding back its goal to improve software tran...
Protecting ML models running on edge devices and mobile apps
Machine Learning models are a significant investment in competitive advantage; thus, companies are willing to walk the extra mile to protect them. ML model security is even more critical...