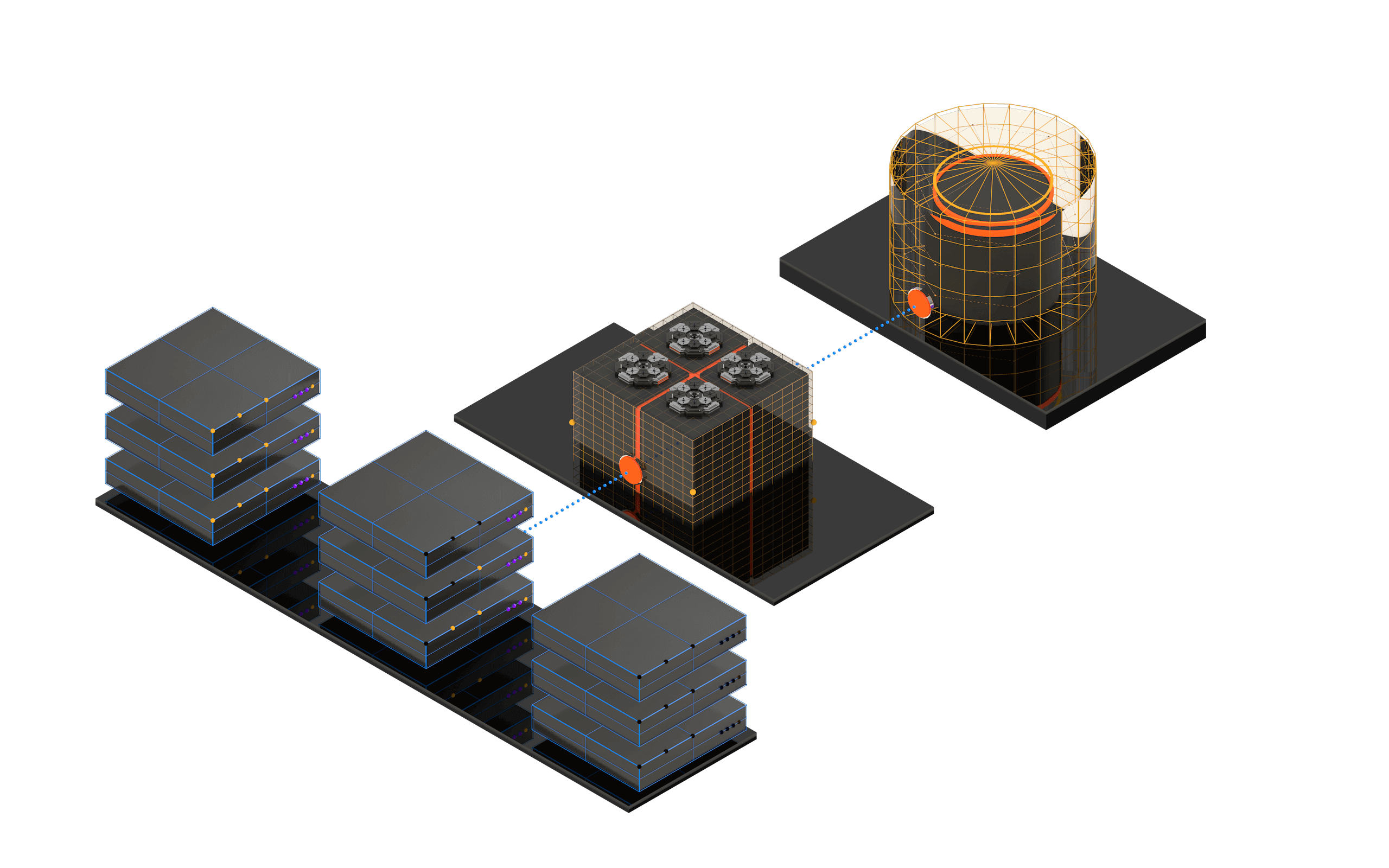
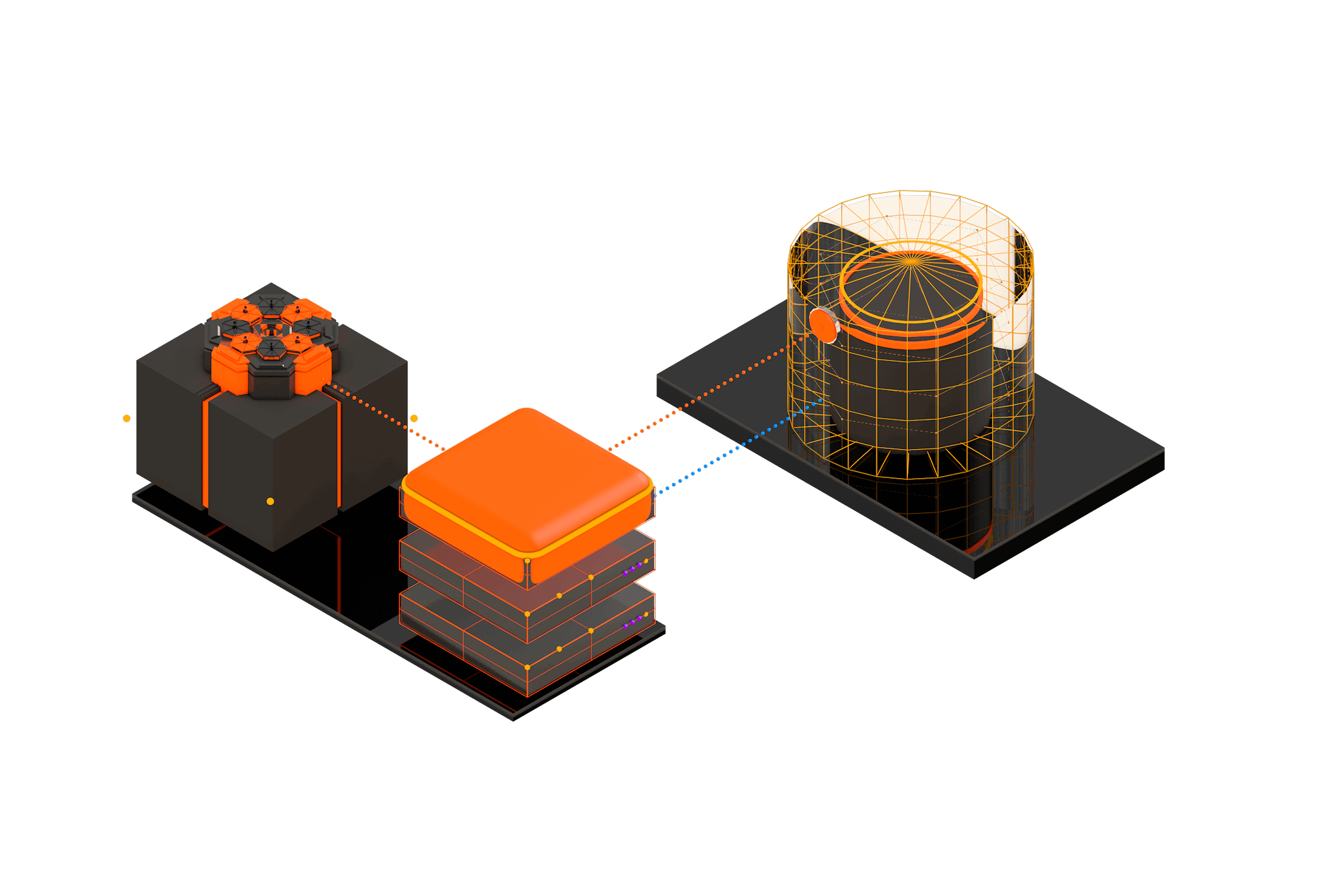
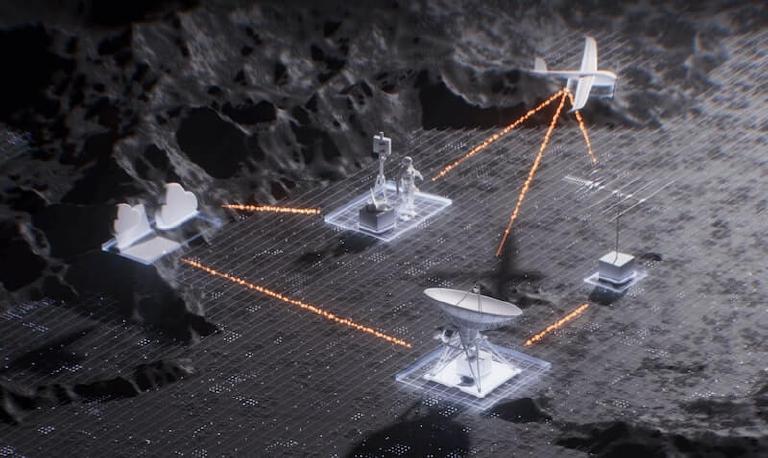
Acra scales and adapts with sensitive data flow
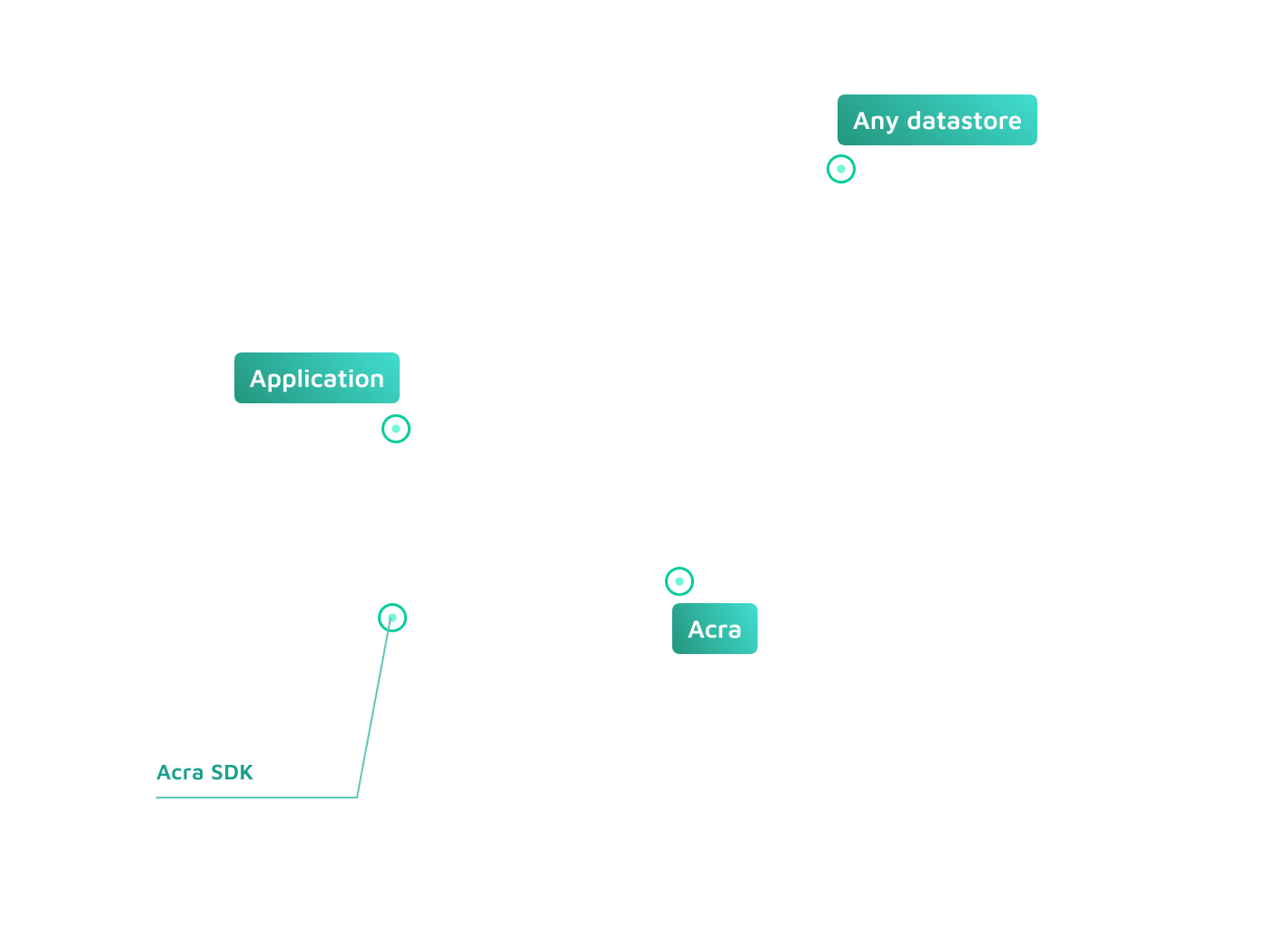
Acra blends well with your application as SQL encryption proxy (AcraServer), encryption-as-a-service API (AcraTranslator), proxy service for any API (AnyProxy), or in-app SDKs. Wherever your data is, Acra is designed to be nearby, enforcing appropriate security controls on your sensitive assets.
Main usage scenarios #
Acra can be used in many ways, yet there are several main distinct security challenges our customers and open-source adopters choose Acra for.
Application level encryption
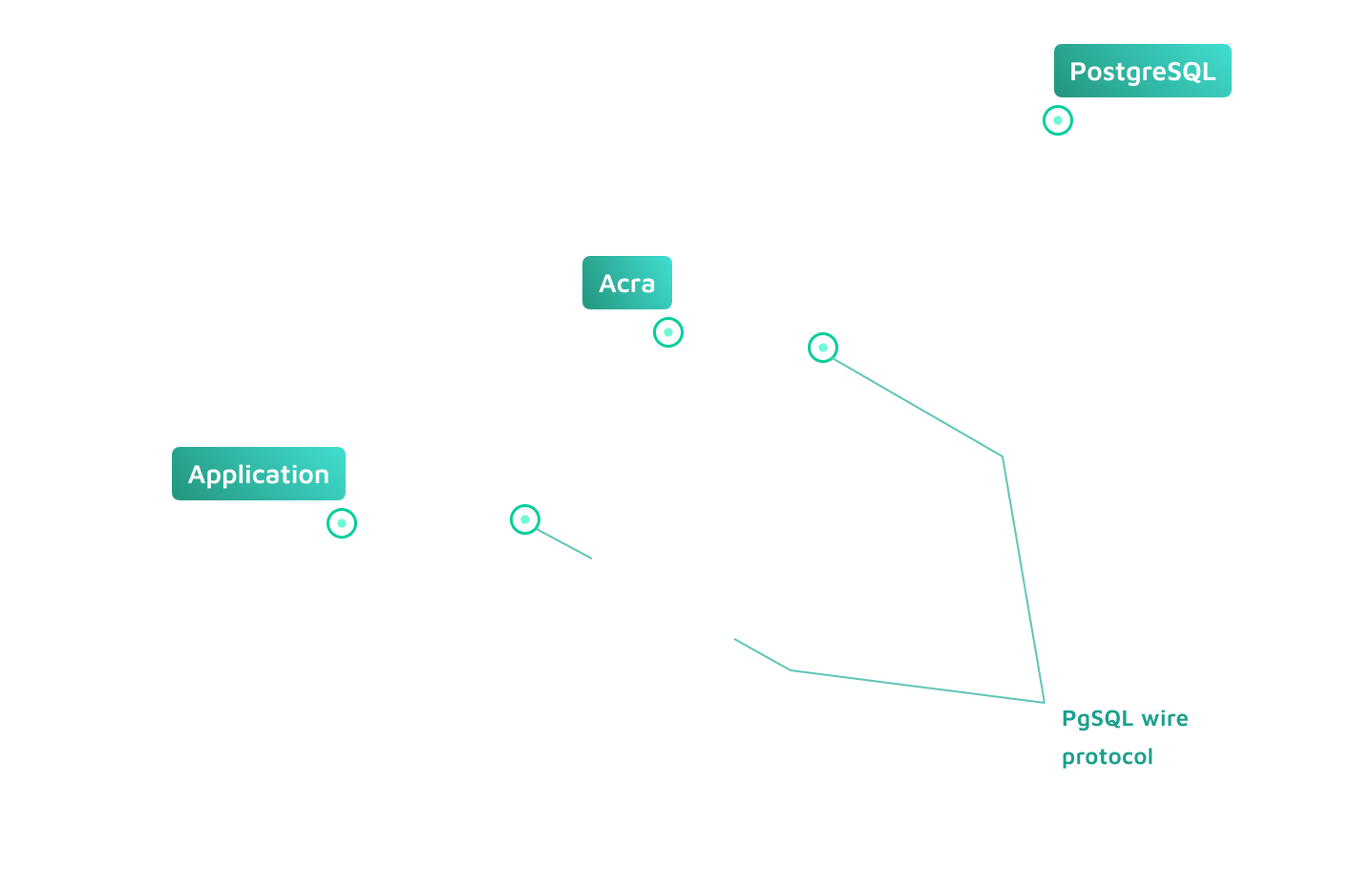
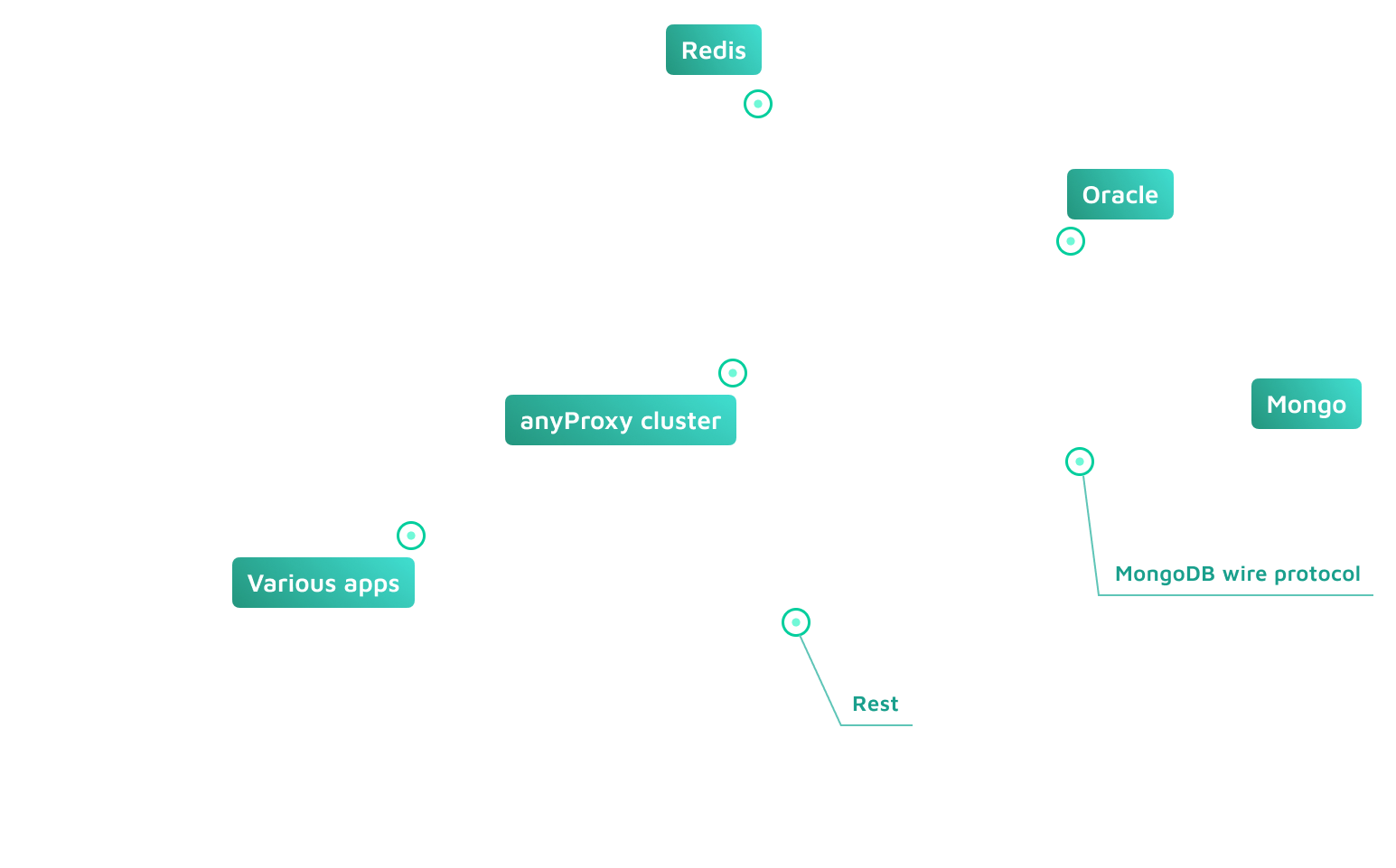
Acra enables field level encryption on application layer as a database proxy (PostgreSQL / MySQL wire protocol), as an API service or a client-side SDK. Choose what fits your use case best.
Sensitive data vault
Acra is equipped with tools to detect data leaks, unauthorised access, and abnormal access patterns using techniques like request analysis, honey tokens, verifiable audit logs, etc.
Database encryption
Acra SQL Proxy acts like a regular SQL database, while running all the necessary security operations under the hood. Data encryption is transparent for the application.
Build security solutions that meet your unique needs
Proven across industries and apps
- Fintech, banking, and neobanks
- Transaction processing systems
- Critical infrastructure / CNI
- SaaS platforms
- Documents exchange (VDR)
- Healthcare records exchange (EHR)
- Industry enterprises, SCADA / ICS
- IIoT / IoT
- Any apps that operate on sensitive or personal data
Solve many challenges with one flexible solution
- Low-footprint security upgrade
- Address many data security risks together
- Usable protected data
- Data security in multiple environments
- Data security in the cloud
- Address privacy requirements
Achieve full regulatory compliance
- GDPR, LGPD
- DPA encryption requirements
- PCI DSS
- DPB
- PSD2
- CCPA, CPRA
- FISMA
- HIPAA / HITECH Act
- FFIEC
- And others
See Acra GitHub for more docs and examples.
More than data at rest encryption, more than TLS #
Role-based access
control (RBAC)
Database privilege abuse
- • Violation of least-privilege (POLP)
- • Stolen credentials
- • Violation of least-privilege (POLP)
- • Stolen credentials
Data access restricted based on user role. Effective when configured properly and credentials are stored securely.
Network snooping, MitM
- • Packet sniffing
- • IP / DNS spoofing
- • Packet sniffing
- • IP / DNS spoofing
Not addressed by this security feature
Data theft
- • Physical access to database host
- • Database file exposed
- • Physical access to database host
- • Database file exposed
Not addressed by this security feature
Access to database
- • Memory dump analysis / scraping
- • Privileged access to database host
- • Memory dump analysis / scraping
- • Privileged access to database host
Not addressed by this security feature
TLS encryption
Database privilege abuse
- • Violation of least-privilege (POLP)
- • Stolen credentials
- • Violation of least-privilege (POLP)
- • Stolen credentials
Not addressed by this security feature
Network snooping, MitM
- • Packet sniffing
- • IP / DNS spoofing
- • Packet sniffing
- • IP / DNS spoofing
Data is encrypted for transport over a trusted network connection. Effective when TLS best practices are followed.
Data theft
- • Physical access to database host
- • Database file exposed
- • Physical access to database host
- • Database file exposed
Not addressed by this security feature
Access to database
- • Memory dump analysis / scraping
- • Privileged access to database host
- • Memory dump analysis / scraping
- • Privileged access to database host
Not addressed by this security feature
FS / DB at rest
encryption or TDE
Database privilege abuse
- • Violation of least-privilege (POLP)
- • Stolen credentials
- • Violation of least-privilege (POLP)
- • Stolen credentials
Not addressed by this security feature
Network snooping, MitM
- • Packet sniffing
- • IP / DNS spoofing
- • Packet sniffing
- • IP / DNS spoofing
Not addressed by this security feature
Data theft
- • Physical access to database host
- • Database file exposed
- • Physical access to database host
- • Database file exposed
Encrypted data on disk remains encrypted unless an attacker has access to the encryption key(s).
Access to database
- • Memory dump analysis / scraping
- • Privileged access to database host
- • Memory dump analysis / scraping
- • Privileged access to database host
In some cases if configured correctly
Acra field
level encryption
Sensitive data is encrypted on a field level.
Data stays encrypted at all times on the database host and in network transit.
The database host doesn't have access to the decryption keys or ways to decrypt data.
Even in case of leakage, all data is encrypted.
Security responsibility is shifted to Acra and key storage.
Address concerns quickly
Wondering if Acra will solve your challenge? Let’s find out together!
Our team will provide you a detailed technical description, answer your questions, assist in optimising sensitive data flows, and help you in evaluating Acra.
Data securitybuilding blocks
Plug various Acra components where necessary or use Acra’s proxies as choke points. Acra provides a unified set of data security controls you can use across your application whenever sensitive data needs protection.
Address security risks conveniently
Make developers life easier
Acra contains a set of highly adaptable components, so you don’t need to spend years on the development of home-brewed cryptographic solutions. Acra supports modern tech stack (databases, ORMs, backend frameworks), and once integrated it just works.
Build your solutions faster
Bring your secure product to the market faster. Acra is easy to integrate, deploy, configure, and use without significant changes in existing architecture. Start small with only necessary security modules, add new components when your product grows.
Get a fair price
You can choose different Acra configurations: from a free Acra Community Edition to a highly customized Acra Enterprise solution. We assist with integration, optimisation and provide several support tiers. You can choose the payment plan that fits your use case: from fewer components to a full spectrum of premium features and 24/7 solution support.
Reduce risks with support and assistance
Reduce extra risks and frictions with integration assistance and solution support. We help reorganize data flows and configure Acra for your use case while adhering to the internal and external procedures and specific regulations.
Evaluate Acra, your way
a. Free Acra Community Edition
Best for prototyping and small-scale projects.
b. Acra open-source engineering examples
Learn how easy it is to integrate Acra data protection into an existing application.
c. Free evaluation playground for popular use cases
As a result, your team knows more about Acra functionality and security benefits it brings into your project.
d. Paid PoC customized for your use case
As a result, your team is confident that you can attain your security objectives with Acra prior to buy-in.
Licensing and Pricing #
Acra Community Edition
Cryptographic data protection suite with all core security features. Best for prototyping and small-scale projects.
- Encryption and masking
- SQL request firewall
- Basic intrusion detection
- Single configuration policy
Apache 2 license, free forever for non-profit and business use
Acra bespoke solution
Solution built around Acra Enterprise Edition that meets your unique needs and requirements.
- Customized masks & protocols
- Customized behavior
- Use case specific features
- Engineering and architecture support
Pricing depends on included services and varies on a case-by-case basis.
Acra Enterprise Edition
Full spectrum of premium features for large-scale and enterprise deployments.
- All Acra features and controls
- Various support tiers
- DevOps / SRE tooling
- Policy management
Pricing depends on number of deployments and features requested. Starting at $10000 annually
| Acra CE | Acra EE | Bespoke Acra EE | |
|---|---|---|---|
| TL;DR | You take open source Acra, configure and deploy it. | You take Enterprise Acra, we assist with configuration, policies, deployment, support. | You take Enterprise Acra, we customize, support and update custom Acra for you. |
| Best for | Small businesses with Ops team. | Enterprise businesses, multiple apps. | Complex products with specific requirements. |
| Encryption | |||
| Field level encryption
AES-256-GCM for each selected database cell. | |||
| Fast and reliable crypto
Acra uses two crypto-envelopes: AcraBlocks and AcraStructs. AcraBlocks are fast symmetric containers, encrypted and decrypted on the Acra side, AES-256-GCM. AcraStructs are asymmetric containers, suit best for client-side encryption and Acra-side decryption, AES-256-GCM + ECDH. | |||
| Simple searchable encryption
Search data without decryption. Based on AES-GCM and blind index approach. Designed for exact queries. | |||
| Anonymization / Masking
Use full or partial masking to remove or mask sensitive data. | |||
| Tokenization
Substitute sensitive data with a token and match it to original only when needed. | |||
| Encryption preserving data format
Preserve data storage format while protecting the data by combining encryption and tokenization. Acra produces tokens that match desired row type/format and replace sensitive data with them. Corresponding plaintext gets encrypted and stored outside format-limited tables. | |||
| Flexible searchable encryption
More flexible and complicated searchable encryption, supports PREFIX and SUFFIX search. Resilient to statistical attacks. | |||
| Custom masking & tokenization formats
Customize masks and tokens format to make sensitive data indistinguishable from other data. | |||
| Custom crypto-primitives support
LibreSSL, BoringSSL, FIPS-compliant, GOST/DSTU compliant, HSM. Acra allows the use of HSMs and external crypto-primitives to comply with local regulations. | |||
| Key management | |||
| Basic key management utils
Key generation, key export and backup, database rollback. | |||
| Key rotation without data re-encryption
Rotate key encryption keys without re-encrypting the data. | |||
| Key management configured for your use case
Custom configuration based on your application behaviour and database layout: custom crypto-periods, compliance with NIST SP 800-57 recommendations. | |||
| KMS support
Amazon KMS, Google Cloud KMS, Hashicorp Vault, Keywhiz, HSMs and others. | |||
| Data leakage prevention | |||
| SQL request firewall
AcraCensor – Acra’s Request Firewall enables to verify all queries to the database against a set of rules and reactions. | |||
| Poison records / honeytokens
Acra puts special data blocks in database tables that look like regular encrypted records, but once they’re requested through Acra, it raises security alarms and halts decryption. | |||
| Arbitrary patterns
Acra can be used as conventional DLP for the database, making sure that chosen patterns or data blocks never pass Acra without an alarm. | |||
| API form factors | |||
| AcraServer: transparent SQL database proxy
Database proxy that exposes Acra’s functionality by parsing traffic between an app and a database and applying security functions where appropriate. | |||
| AcraTranslator: encryption-as-a-service API
API server, that exposes most of Acra’s features as HTTP / gRPC API with traffic protection. | |||
| AnyProxy: gateway to the encryption layer
API server and client-side SDKs that work as a gateway to the encryption layer for several applications and databases. | |||
| Bulk API for AcraTranslator
Typically, AcraTranslator API methods allow one exact operation to be performed per call. Bulk API allows performing multiple parallel operations within single network request. | |||
| SDK for AcraTranslator
SDK for AcraTranslator that encapsulates API for more convenient usage. | |||
| AcraConnector: transport authentication and encryption
Optional client-side service for authentication and transport encryption. | |||
| AcraWriter: SDK for client-side encryption
Client-side SDK for encrypting data on application side. Supports numerous client-side languages. | |||
| AcraReader: SDK for client-side decryption
Client-side SDK for decrypting data on application side. Supports numerous client-side languages. | |||
| Extensions | |||
| SCADA & ICS security kit
Acra provides modules for secure data aggregation in large-scale ICS/IIoT/SCADA systems and providing gateways between SCADA datastores and external IT systems. | |||
| Databases | |||
| SQL databases
AcraServer supports database encryption for PostgreSQL wire protocol and MySQL wire protocol. MySQL 5.7+, PostgreSQL 9.4+, MariaDB 10.3. | |||
| Major NoSQL / KV datastores
MongoDB, Redis, Cassandra, TimescaleDB. | |||
| Cloud RDBMS support
Google Cloud SQL, Amazon RDS, TiDB, CockroachDB. | |||
| Scalable SQL-compatible DBs
Google Cloud SQL, Amazon RDS. | |||
| Any NoSQL / KV datastore
Any datastore or database with REST API, filesystems, Amazon S3, Google Cloud DataStore. | |||
| Integration, deployment | |||
| Multiple client-side languages and platforms
Almost any application can talk to Acra. Browser: WASM/JavaScript. Mobile: Swift/ObjC, Java/Kotlin. IoT/embedded: C++, Rust, C. Web apps: Go, Python, Ruby, Java, C++, PHP, Node.JS. | |||
| Multiple server-side languages and platforms
Almost any application can talk to Acra. AcraServer and AcraTranslator can run on CentOS, RHEL, Debian, Ubuntu. | |||
| Docker support
Pure Docker. | |||
| Orchestration tools support
Docker Swarm, Compose, Kubernetes. | |||
| Simple logging, metrics, tracing
Acra produces eloquent logs, metrics and tracing events. | |||
| Exportable logging, metrics, tracing
Compatibility with Google StackDriver, ELK, Prometheus, Datadog, Graylog, etc. | |||
| SIEM support
ExaBeam, QRadar, Splunk. Acra’s security log is specifically pre-configured to be helpful to SIEM/SOC operators in building analytics and automation around security events. | |||
| Crypto-signed audit log (verifiable audit logging)
Acra’s audit log covers access, security events, ties sessions to consumers and extends application level audit log with strong evidence. | |||
| Load balancing support
HAProxy, DB poolers, Round Robin, cloud load balancers. | |||
| Support for all major IaaC tools
Chef, Ansible, SaltStack, Hashicorp stack, GCP, AWS scripts. | |||
| Custom K8S chart or docker-compose
Create, customize or optimize configuration files for you. | |||
| Policy management | |||
| Single configuration policy | |||
| Managing multiple policies
To enable Acra to be more flexible security control, apply different policies based on keys, origin and other factors, Acra Enterprise Edition features policy engine. | |||
| Creating custom policies
Creating, customizing or optimizing policies. | |||
| Assistance | |||
| Assistance with deployment | |||
| DevOps / SRE tooling | |||
| Customer support | |||
| Strict SLA | |||
| Acra managed solution
We assist your team in integration and managing Acra for you | |||
| Acra bespoke solution
We customize Acra with behaviour, modules, masks, protocols, crypto-primitives, databases support that are best for your exact architecture and use cases. | |||
Acra CE
TL;DR
Best for
with Ops team.
Encryption
Key management
Data leakage prevention
API form factors
Extensions
Databases
Integration, deployment
Policy management
Assistance
Acra EE
TL;DR
we assist with configuration, policies, deployment, support.
Best for
multiple apps.
Encryption
Key management
Data leakage prevention
API form factors
Extensions
Databases
Integration, deployment
Policy management
Assistance
Bespoke Acra EE
TL;DR
we customize, support and update custom Acra for you.
Best for
specific requirements.
Encryption
Key management
Data leakage prevention
API form factors
Extensions
Databases
Integration, deployment
Policy management
Assistance
Choose your Acra
Contact us
Get your Acra up and running fast with the help of engineers who built it!
Ready to start or need more information? Let’s discuss how Acra can solve your data security risks with our assistance in defining goals, integration, configuration, and deployment.